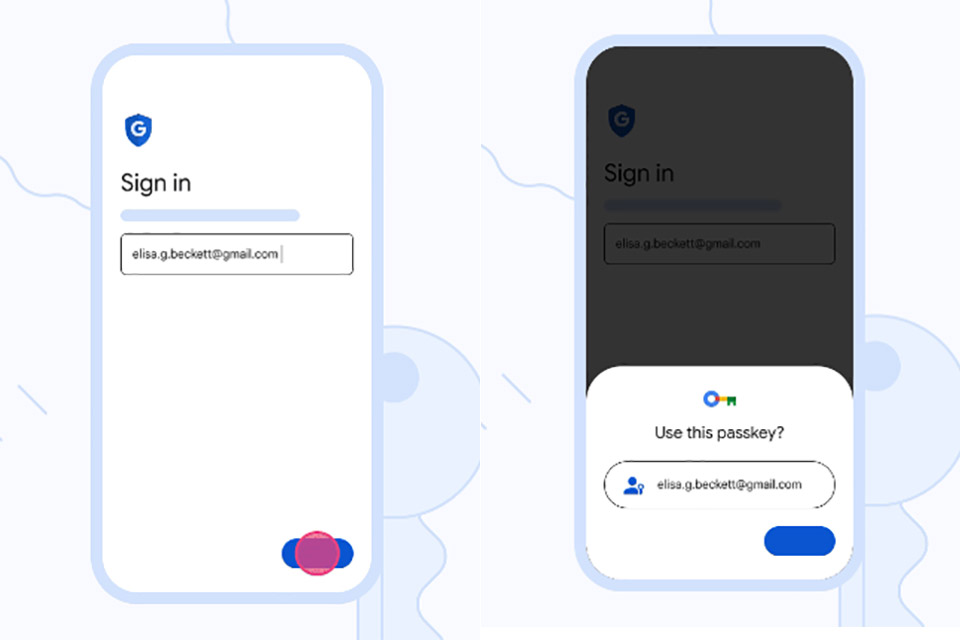
Google Passkeys has begun rolling out, and it lets users sign in to apps as well as websites without using any kind of password. Put simply, passkeys work the same way as unlocking a mobile device using a fingerprint, face scan or screen lock PIN, which means they are resistant to online attacks such as phishing.

Before typing a pin number of password on a public computer, make sure to wear gloves, or else the ThermoSecure system may be able to guess it based on the heat left from your fingertips. Computer security experts from the University of Glasgow developed this system to show how thermal imaging cameras can be used by nefarious actors to steal passwords on a computer keyboard, smartphone / tablet, or an ATM keypad.

Josep Pi Rodriguez of IOActive discovered a new NFC relay attack that could potentially be used by thieves to steal a Tesla Model Y in seconds without its owner noticing. These near-field communication (NFC) cards enable Telsa owners to unlock their vehicles and start the engine by simply tapping the it against embedded reader in the driver’s side body of the car.

Cybersecurity researcher Marcus Hutchins shows how to spot tiny hidden cameras concealed inside of fire alarms, clocks, and USB chargers that may be inconspicuously placed throughout your next Airbnb rental. One of the easiest methods is to just shine a bright light on any questionable equipment or electronics placed in optimal locations that could be possibly be used for spying purposes.

Yubico, maker of hardware authentication keys, has just unveiled the YubiKey 5Ci. It’s the world’s first security key designed with both USB-C and Lightning connectors on a single device, making it compatible with iOS, Android, MacOS, or Windows devices. This means you can use it to secure 1Password, Bitwarden, Dashlane, Idaptive, LastPass, and Okta iOS apps, along with additional services accessed through the Brave iOS browser app. Read more for a video and additional information.

Created by security expert Troy Hunt back in 2013, Have I Been Pwned? is a website that lets you check if your personal data has been compromised by data breaches by collecting and analyzes hundreds of database dumps. It allows users to search for their own information by entering their username or email address, with the option to sign up to be notified if they’re detected in future dumps. One thing you may not know is that a password like “ji32k7au4a83” is more commonly used than you think, according to Robert Ou, and it’s a simple reason actually, as it’s comprised of characters from the Zhuyin Fuhao system for transliterating Mandarin. Read more to see a picture of the Chinese keyboard, and how the characters come about.

Photo credit: Twitter
You may have never heard of the Cellebrite UFED (Universal Forensic Extraction Device), but it’s used by the police, FBI, Department of Homeland Security, etc. on smartphones, memory cards and more. Typically, current models cost around $15,000, but cybersecurity researcher Matthew Hickey managed to pick up several UFEDs from eBay for just $100 each. He found details on what phones law enforcement officials searched, when they were accessed and the data retrieved. Read more for a video showing how it works.

Let’s face it, with all of the phishing scams and other security-related issues nowadays, it’s a no brainer to enable multi-factor authentication for just about any important account you use, Fortnite included. Epic Games wants to reward those who do enable two-factor authentication (2FA), which requires you to enter an extra code sent to a secondary device during the sign-in process, by sending them a Heartspan Glider. Read more to find out a way to send this to a friend who hasn’t yet enabled this feature.

Photo credit: Akami
Another day, another online phishing scam, but this one makes use of Google Translate to make it appear legitimate at first glance. Simply put, these group of hackers masks the phishing with a Google Translate URL (www.translate.google.com), and once the victim clicks on that link, they will be redirected to the Google Translate portal, which load the phishing page with the Google Translate toolbar up top in an iframe. One more thing to note is that the sender is “[email protected]” and not even a Google or GMail address. Read more to see what that page looks like.

Photo credit: Valentina Palladino
For those who receive FaceTime calls on a regular basis, it may be time switch off that function, or at least for now if you’re running iOS 12.1+. A newly discovered bug lets you eavesdrop on the iPhone or Mac you’re calling even without the other party answering. Simply start a FaceTime call, swipe up to add a person, and then choose your own phone number to create a group FaceTime call. If you automatically answer the call for the first person, both the caller and the original recipient will be able to hear one another, or if the caller is quiet, this lets them eavesdrop if the recipient did not hear the original call. Read more to see the bug in action.



