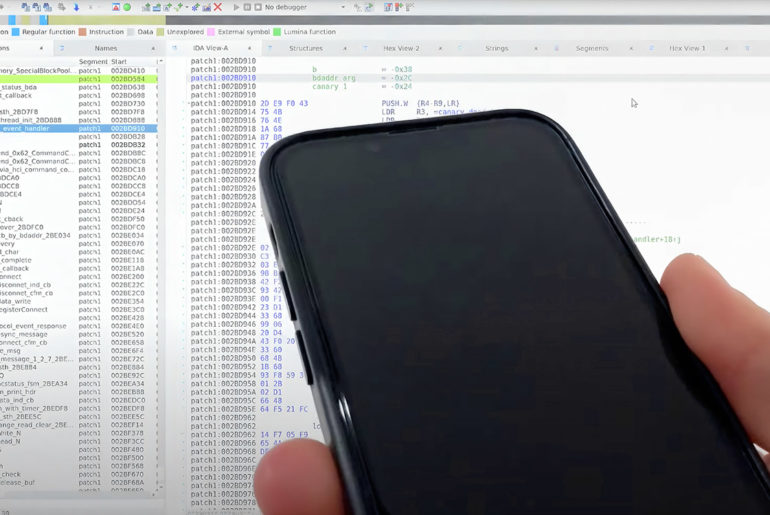
Just when you thought that Apple devices were safe, ‘Evil Never Sleeps’ iPhone malware comes along, or at least a proof of concept. Yes, it can actually run when your iPhone is powered off because the hardware inside is still running in low-power mode, thus explaining how you’re able to locate it using “Find My” or other tracking tools.
The critical hardware component that this malware uses is the Bluetooth chip, which runs in low-power mode (LPM), along with the chips for near-field communication (NFC) and ultra wideband. These components run for approximately 24-hours after the iPhone has been turned off. Thankfully, this malware is only useful on jailbroken devices, but does show the possibilities of what nefarious developers could do. In somewhat related news, Apple is allegedly already testing USB-C iPhones.
- Powerful Productivity: AMD Ryzen 3 3350U delivers desktop-class performance and amazing battery life in a slim notebook. With Precision Boost, get up...
- Maximized Visuals: See even more on the stunning 15.6" Full HD display with 82.58% screen-to-body, 16:9 aspect ratio and narrow bezels
- Backlit Keyboard and Fingerprint Reader: Biometric fingerprint reader and Windows Hello sign-in options help keep your Acer PC secure
The current LPM implementation on Apple iPhones is opaque and adds new threats. Since LPM support is based on the iPhone’s hardware, it cannot be removed with system updates. Thus, it has a long-lasting effect on the overall iOS security model. To the best of our knowledge, we are the first who looked into undocumented LPM features introduced in iOS 15 and uncover various issues,” said the researchers.